cloud, cloudsecurity, Cloud Enterprise Architecture, cloud migration, Case Study, Cloud Networking, data engineering, Big Data, Business Intelligence, Resource Management, Data Management, Techquity
The Need for Better Cloud Network Security

Transitioning traditional data center environments to the cloud offers federal agencies huge advantages in performance and flexibility. Agency services can’t effectively scale or adopt new capabilities and meet transformation goals without migrating to the cloud.
But, for all its benefits, the move to the cloud is also creating serious vulnerabilities due to a lack of clear standards for usage and access.
Most agencies are learning as they go along when moving to the cloud. The movement of IT resources to the cloud has preceded a management structure to monitor and control how cloud resources are provisioned and used.
Unlike a data center environment, it’s very easy for development teams to spin up new cloud resources, forget about them, and then move on to the next urgent task.
Teams also size cloud resources too large based upon the legacy technical specifications coming from on-prem datacenters, instead of starting small and using cloud elasticity for auto-scaling. This results in inefficient use of cloud resources - over-provisioned, over-scheduled, underutilized, or orphaned cloud assets. Even when cloud servers are terminated, the servers’ storage volumes – in a sense virtual hard drives – are often left behind.
From a security perspective, the lack of usage guidelines for hardening, encryption, vulnerability monitoring access can create new vulnerabilities. If these usage guidelines are not known by the cloud users or enforced through cloud governance monitoring, then the security posture degrades rapidly.
The lack of a governance structure that can monitor and manage the move to the cloud has created a wild west-type situation at many agencies. It’s not surprising that the GAO found improper usage of cloud was the most common reason for security incidents in 2019:
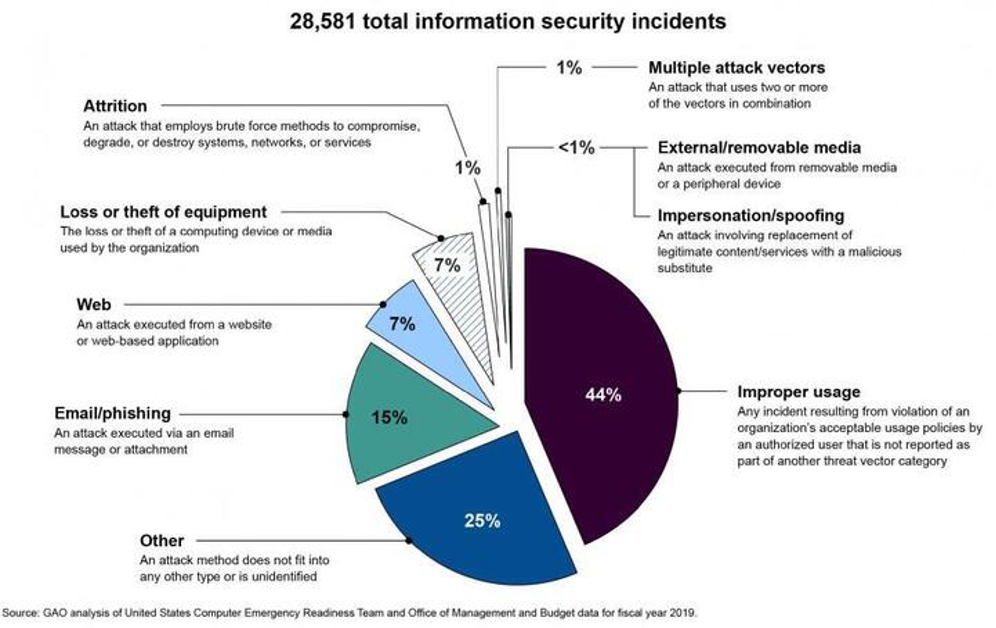
It isn’t just improper usage – which could be innocent in nature – that poses a cybersecurity threat. The lack of cloud governance can also make agencies more vulnerable to external data breaches.
When development teams create cloud resources, they may not fully understand the impact of its related configurations, as was the case in the 2019 Capitol One data breach that enabled access to sensitive records stored in AWS S3 buckets.
The sheer scope of commercial cloud services can also cause confusion for government IT teams. The commercial CSPs continually add new offerings to their suite of cloud products, each offering hundreds of services. To date government agencies only use a small percentage of these, primarily networking, compute, storage, and managed database services, i.e., Infrastructure-as-a-Service (IaaS) and Platform-as-a-Service (PaaS) services.
As government development teams begin to expand their use of cloud services, there is the danger they choose services that have not been FedRAMP approved. All the major CSPs try to make it clear which services are and are not approved, such as this page from Amazon Web Services. But there is no policy enforcement provided by the CSPs that prevent an agency from choosing an insecure service.
Finally, true cloud security can never be accomplished until cloud security is integrated into the overall security posture of the enterprise. AWS, Microsoft, and Google Cloud have all launched cloud-native security centers in the past few years, focused on helping their client manage secure cloud hosting environments.
But these services need to be integrated into the security technology currently used in the agency SOC – typically a Security Event and Incident Management (SEIM) tool such as Splunk. True security requires binding together the threat landscape from security systems, email, IT/ OT, and business technologies across the entire agency. It’s a massive organization management challenge as much as a technical challenge.
Fortunately, there are foundational best practices that can act as cloud standards to bring stronger security and policy governance to the current wild west of government cloud. I will speak to those in the next article in this blog series.
Want to ace your FITARA scorecard?
No one wants to testify before Congress on why their FITARA scorecard grade went down. Access our digital resource to see how you can ensure your agency is prepared.

Aaron Kilinski
Aaron Kilinski, Principal and Chief Technologist is a multi-disciplined and energetic innovator committed to delivering business results that leverage cutting-edge ideas and state-of-the-art technology to STS.





